Advocating Domestic Extremism - Cops on Indymedia - An Exposé
Birmingham IMC | 23.01.2011 19:53 | Indymedia | Policing | Repression
On April 27th, 2010, a comment appeared on the Indymedia UK newswire entitled Don't use SPEAK as a model. The comment, on an article entitled New animal lab at Leicester; New nationwide campaign to start urged readers to respond to the campaign by "Model{ling} the campaign on a successful AR campaign such as Hillgrove cats or Darnley(sic) Oaks etc". Readers familiar with those campaigns will be aware that the campaigns are alleged to have included violent actions against individuals, including a a letter bomb in the Hillgrove Cats campaign, and the removal of Gladys Hammond from her grave.
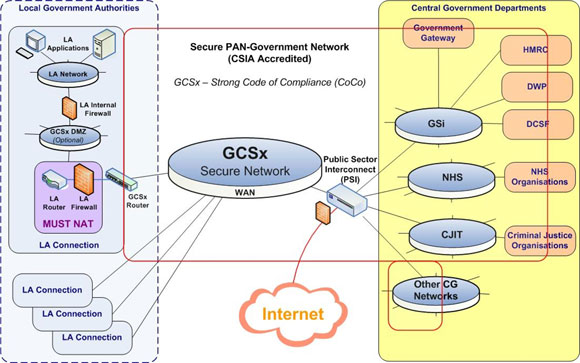
http://www.govconnect.gov.uk/what-is-gcsx.php
Posts which incite others to commit violent acts are a risky business for Indymedia Collectives. In early 2009 Indymedia UK had one of its servers seized after a comment was posted to the newswire, with the home address of the judge from the Stop Huntingdon Animal Cruelty (SHAC) trial. An individual was arrested, and to this day the police continue to hold the server, along with personal belongings of the arrestee. In 2005, a local collective, Bristol Indymedia had their server seized from the home of an activist, after a site user complained to the police about an anonymous post to the Bristol Indymedia newswire, which reported an 'action' in which objects were dropped onto a freight train carrying new cars somewhere near Avonmouth.
In both those cases Indymedia, because of stringent rules designed to protect user anonymity, was absolutely unable to provide IP addresses to anyone as the system does not log IP addresses. Today however, we are able to state categorically that the comment containg the incitement was one of a long list of posts which have come from a Government Secure Intranet known as Gateway 303, a state network which provides a secure proxy network behind which state agents can maintain their anonymity. Other posts from the same government secure intranet have targeted individual activists, put out information about activists that is not in the public domain, attacked campaigns, and urged the disruption of peaceful protests with Direct Action. The main targets of these many articles and comments have been Environmental Campaigns and Animal Rights campaigns and activists. Whilst we do not have any way of identifying from which computer behind the Government Secure Intranet these posts came, we would hazard a guess that they came from someone who has links to The National Extremism Tactical Coordination Unit known as NETCU, a shady body which has so far evaded accountability because it has been set up as a private limited company despite the fact it is staffed by serving police officers, and funded by the Home Office.
We have decided to publish a list of all posts that we know were made from Gateway 303 so that activists can see for themselves some of the tactics that agents of the State have used to disrupt, and provide disinformation on Indymedia, and which campaigns and activists they have targeted. With this information, we believe that the state should be able to identify their own agent-provocateurs, and furthermore that this exposure of the posts by State Agents undermines the state itself in a number of ways. It shows once again that the so-called "forces of Law and Order" are infiltrated with unprofessional individuals who are prepared to go to great lengths to set-up individuals and protest campaigns, and that despite all their many claims, parliamentarians are unable to take effective action to weed out the 'bad apples' they say are the problem. It undermines attempts by the Crown Prosecution Service to smear defendants by pointing to anonymous postings on Indymedia. Judges will now have to take into account that there is clear evidence that Indymedia UK is abused by State Agents to harass campaigns and individuals, and to incite the very kind of 'Domestic Extremism' that outfits such as NETCU were set-up to specifically stop. We wonder if some of their own posts have been used by NETCU to bolster their own importance and to justify higher levels of funding than they might otherwise receive. We cannot know for certain, but can strongly suspect, that there have been other state posts which have come from non-filtered IPs, and that by going public on these posts, we have made public the propensity of the State to harass campaigns and activists through abuse of open publishing sites.
How does Indymedia UK know where these posts came from, when it always said it doesn't log IPs?
It is absolutely true that Indymedia does not log IPs - by which we mean the IP Addresses of those who use the website are not recorded for the purposes of protecting their privacy. However, what has never been openly stated before is that the CMS system we use has a number of anti-abuse measures which include the ability to monitor for particular IP addresses and log their behaviour. The key here is that IP addresses are never written to the hard disk - they are briefly held in the RAM (i.e. temporary) memory only. Only when particular IP addresses are identified as persistent abusers are they applied to filters. There remains no general practice of logging each and every user. Once the anti-abuse measures are turned off, any IP addresses identified are automatically wiped from the virtual memory and, as they were never written to the hard disk, no amount of forensics would ever be able to find them.
In this particular instance however, the filter for the Gateway 303 IP was manually added after site admins became aware of a post on Animal Rights Copwatch which revealed that someone posting from Gateway 303 had posted to their site, posing as an Animal Rights activist. This allowed all posts from Gateway 303 to be identified and each post was flagged with an internal comment that identified it as a post from Gateway 303.
In the early days of Indymedia UK, which recently celebrated it's 10th Birthday, site admins believed that they would never be able to gain the trust of posters, if the range of anti-abuse measures were made public. As is often the case, once a body has failed to be completely open about something, it becomes 'the elephant in the room' and so a situation was created where the new and current admins were actively blocked from bringing these measures into the open. The stalemate continued until now, with site admins proposing a new approach of coming clean about the measures that are in place, and others in the collective blocking this.
The dilemma was brought to a head when it became clear that the state was exploiting the stalemate to attack campaigns and activists, and the most recent posts meant that the calls to expose these attacks became louder. We sought to convince people within the collectives that activists are now much more aware of how the internet works, and many have direct experience of working on sites which have a range of anti-abuse measures. We also argued that continuing to gloss over the reality in a misleading way was detrimental to Indymedia UK, and that there was no small likelihood that at some stage we could be outed. Furthermore, we argued that as a group we have a duty to defend campaigns and activists that are being targeted by the state, in exactly the same way that people have supported us when we have experienced state repression, and that we could no longer justify allowing state agents to abuse Indymedia UK, by glossing over what we knew was happening.
However the state chooses to respond to this revelation, the truth remains that there is no written log of IP addresses, and that no amount of duress will enable any IMC admin to reveal information that quite simply is not available to them. We will endeavour to produce an article detailing how our anti-abuse measures operate, as quickly as possible.
Be Cleverer than NETCU - mask your identity.
Posts on Indymedia have often urged people to protect themselves from the cameras and Police Intelligence Units by masking up at public demonstrations. Those activists who have taken steps to avoid detection of covert actions before, during and after they take place, are well advised to take other steps to avoid detection when posting about those actions . This is because we know that we cannot guarantee that there are not other ways for the state to trace your computer activity.
In our post-server seizure article in February 2009 we suggested the following steps to to improve your security when using the IMC-UK website:
- Only post stuff to Indymedia that won't get you in trouble.
- Use Tor - an application that allows you to anonymise your IP address. Bear in mind that it is not 100% safe - see these Tor caveats. The safest way to use Tor is probably via a live CD or USB stick, see the The (Amnesic) Incognito Live System, which is designed so that "all outgoing connections to the Internet are forced to go through the Tor network" and "no trace is left on local storage devices unless explicitly asked".
- Don't post it on Indymedia, post it on wikipedia or blogspot or... well those two aren't that good, but cryptome is pretty secure and better security than Indymedia in a number of ways.
- Set up your own open publishing platform: the more the merrier.
- Don't post anywhere on the internet.
We take this opportunity to urge you to look out for workshops on internet security, and to read up on proxies, anonymisers and SSL.
We issued this statement when the server was seized last year:
Indymedia takes your privacy seriously and works hard to ensure that the strictest security measures are in place. However, while we hope that everybody trusts our commitment to protect our users - and thus our technical and security procedures - we also understand that the measures we take may not be easily understandable by non-techs. In this article we have therefore tried to explain some of the measures we take and why we take them. We end with a reiteration of our commitment to the global Indymedia Principles of Unity - and particularly want to highlight Principle 4:
4. All IMC's, based upon the trust of their contributors and readers, shall utilise open web based publishing, allowing individuals, groups and organisations to express their views, anonymously if desired.
We re-affirm that commitment to your security now, and we apologise for allowing a situation to develop where we did not inform you of the full picture. This article marks out our commitment to take steps to avoid allowing a similar situation to arise.
Birmingham IMC
Additions
Distraction?
24.01.2011 01:41
These are just vague legal implications. The most important thing is that it reminds people of the lengths the state goes to in order to undermine us. It should act as a wake up call to everyone who thought that Indymedia was a pure source of information for activists. Everything on here should always be taken with a pinch of salt. This proof of police involvement should once again instill caution into people and in doing so make such police tactics automatically fail.
But not everyone is seeing it this way. A large amount of postings are attacking Indymedia for releaseing such information. I've got to ask why? I can come to only two possible conclusions. The first is that the people complaining can't see the wood from the trees. In order to stick to precious principles, they are failing to see the importance and the implications behind the information that Indymedia have released. perhaps they should remember that we don't live in an ideal world yet and at times we have to respond and fight back (even if the fight back only involves releasing information).
The other possibility is that the whingers are trying to act as a distraction. They are attempting to move the emphasis from the information released and the fact that the police are involved in organised trolling. Instead they are trying to focus on attacking and turning peopel against indymedia and activists against each other. Just like the many of the posts from the police were attempting to do. I'm sure everyone can draw their own conclusions on what type of people would want to do this and why they would do this!
J. Connolly
Comments
Hide the following 19 comments
Is this an official statement from IMC UK?
23.01.2011 21:02
The fact this appears as a promoted article would suggest that this previously censored article no receives the stamp of approval from IMC UK and an official admission that site admins had previously conspired to misled users about the potential to log IP details.
about time
Official statment?
23.01.2011 21:13
But at least some regional collectives are making their views on this clear:
Advocating Domestic Extremism - Cops on Indymedia - An Exposé
Birmingham IMC | 22.01.2011 16:02
Gateway 303: Police Disinformation on UK Indymedia
Sheffield Indymedia | 22-01-2011 22:35
times up
re: Is this an official statement from IMC UK?
23.01.2011 21:26
Really it's irrelevant whether they do or don't save a full log of IP addresses - you have no way of knowing if they are telling the truth anyway. Always assume you are being logged, even if someone claims otherwise.
As many of the cop posts are just fairly factual accounts of news, I wonder if they were just trying to get a discussion going so they could see who was commenting and what was being said. I wouldn't be surprised if someone like NETCU is in with Indymedia's ISP and is fully logging the time and date of every IP address that visits the site, anyway.
I thought it was common knowledge that Indymedia could identify trolls and cops by IP address and block them from disrupting the site. Not sure why it is such a big deal - maybe it is only cop trolls (now posting from normal IP addresses) that are complaining so vocally?
anon
J. Connolly
24.01.2011 02:40
Here another angle you might want to consider: Perhaps people are concerned or annoyed by the IM disinformation in the first place. Or is that too inconvenient
There is also the plain legal side to consider regarding damages incurred through false statements.
Davvy
@Davvy
24.01.2011 07:55
nowhere does J.Connolly say "basically anyone who criticises the situation must be a policeman or some kind of state agent?"
yvvaD
re: Official statment?
24.01.2011 08:48
"Following the publication of this schnews article, Indymedia London
would like to make it clear that it does not log, monitor or filter
the IP addresses of those who visit or publish on this website. The
hyperactive code that indymedia london and others [1,2] run on does
not have these facilities built into it.
The story published by schnews relates to the website found at
indymedia.org.uk only.
The information published does not apply to any other Indymedia
website, inside or outside the UK. Indymedia websites live on
different servers and use different Content Management Systems, as
well has having different policies and abuse measures.
In fact indymedia london takes the issue of IP logging so seriously
that we do not allow people to embed content like Youtube videos on
the website, since that would make the IP addresses of viewers
available to youtube. Whilst this means Indymedia London may look a
little behind the times in terms of internet development when compared
to other websites, it's simply because we take your online security
seriously.
For advice on these issues including how to publish anonymously see:
tech tools for activists - security in a box - corporate social networking
"Additions are not allowed on this article."
In other words you cannot comment, or ask for, clarifications under the post.
What London Indymedia does not address in their statement, is their own role in the UK Indymedia site and the cover up of the truth about the exisiting anti-abuse measures..
They were most certainly aware that IMC uk had the capability to log IPs, and were also central in writing the misleading statements and articles such as
They now claim that they have no facility for logging IPs on their new site, but until they come clean about what they knew and what they did about the anti-abuse measures on IMC uk, along with the active steps they took to bury the revelations about the anti-abuse ,measures and the posts by cops to Indymedia, I can't see a basis for trusting what they now say.
This attempt to extricate themselves from the mess without coming clean about the part they played in setting it up in the first place, and then maintaining the fiction, does not go far enough.
time to come clean
Finally! Indymedia has stopped lying to us all...
24.01.2011 10:32
Shocking that some people in Indymedia think we should just sit back and allow the police to use and abuse OUR activist tools - and even more shocking that these people didn't think the users and contributors of Indymedia had any right to know about any of it. For this, I'm really disappointed and disheartened. I wonder if this article would've ever reached the public domain if Schnews hadn't run with the story...?
I know the mods are probably worried that people get all hysterical over IP logging - but jesus give us some credit - we are intelligent people who can see the difference between an IP mask and basic logging of all IPs. Fellow activists have been routinely stitched up, falsely criminalised, the cops have faked comments in order to gain more power at protests, and Indy posts have been used against people in their court cases - even though the cops posted the articles in the first place. To hide this information is a disgrace to the name of open, independent media and as a result has actually contributed to innocent people being penalised.
@anon:
"As many of the cop posts are just fairly factual accounts of news, I wonder if they were just trying to get a discussion going so they could see who was commenting and what was being said. I wouldn't be surprised if someone like NETCU is in with Indymedia's ISP and is fully logging the time and date of every IP address that visits the site, anyway. "
This is absolute bullshit and you must know it!! Indymedia have been very clear over their IP logging. You've seriously gotta be on something to actually believe that Indymedia will be in with NETCU.
Better Late Than Never
@Better Late Than Never : Indymedia's ISP != Indymedia
24.01.2011 13:12
"As many of the cop posts are just fairly factual accounts of news, I wonder if they were just trying to get a discussion going so they could see who was commenting and what was being said. I wouldn't be surprised if someone like NETCU is in with Indymedia's ISP and is fully logging the time and date of every IP address that visits the site, anyway. "
@Better Late Than Never
"This is absolute bullshit and you must know it!! Indymedia have been very clear over their IP logging. You've seriously gotta be on something to actually believe that Indymedia will be in with NETCU."
Indymedia's ISP (Internet Service Provider) is NOT the same as Indymedia. In fact they probably have a whole hierarchy of ISPs, any of which has access to all data flowing in and out of their networks. If someone is government hasn't arranged with any of them to monitor Indymedia traffic, they aren't doing their job properly.
anon
Internal contradictions show that this is not the whole truth.
24.01.2011 13:46
However, the text suggests that having come through gateway 303 is proof that it's a cop posting. This is clearly contradictory.
Which is it please? Have you missed out an embarassing part of the story maybe?
marker
Indymedia UK's ISP..
24.01.2011 15:18
Insider
Re:
24.01.2011 15:20
If you read all the information available you would learn that there are posts from gateway-303 which expose information about activists not in the public domain, and which NETCU or another police department would know about.
Insider
Indymedia's ISP is in the USA?
24.01.2011 15:40
a whois on 72.232.204.178 seems to show the ISP is Layered Technologies, Inc. from Texas, USA.
That doesn't invalidate my point though. I'm sure UK filth have good contacts with US filth and can get the FBI or whoever to arrange for the logging of data. From what I read, this is a commonplace occurrence.
Just face it, it is very difficult to be truly anonymous on the internet, which is why this whole furore over Indymedia filtering out trolls is no big deal and a diversion from the real issues. I fully expect the government to identify my IP address from everything I post on Indymedia, unless I use something like Tor.
anon
Some questions
24.01.2011 15:53
FACTS
It appears somebody in government has carried out a concerted campaign of disinformation via the indymedia comments pages (although we don't know for sure if it was an official operation carried out by cops).
It is clear that this information has been available to indymedia uk since last summer but concealed from users due to fear that disclosure would expose that there had been a policy of telling half truths about the use of IP logging.
It is obvious that there was dissenting views about publishing the information and that an indymedia admin went ahead and published it without consent under the pseudo name indyleaks. These posts were routinely hidden from indymedia sites and a filter set up on IMC UK.
SchNEWS obtained the info (either picking up on the indyleaks posts or in collaboration with another indy admin) and published it out of reach of the censorship efforts of indymedia.
Brimingham IMC published the story as a feature on their site while there remained no consensus within the Indymedia UK network to make it a feature on the UK front page.
London indymedia issued a statement trying to distant their own site from fallout over the controversial confession that IMC UK admins had always been able to access to IP logs if they wanted.
Questions:
What is important here? The fact that there appears to have been a government sanctioned campaign of disinfo against our movements via indymedia is obviously important and something which should not have been hidden from the movement for so long. It is shocking that some admins preferred to keep users in the dark rather than risk exposing their own previous dishonesty.
Is the IP logging important? Probably not, the lies around it are more important than the existence of the feature. It is not unreasonable that site admins have access to tools to protect publishing sites from abuse. Such tools don't need to include IP monitoring and IP filters but it is a powerful tool. Lying about it on the over hand is unforgivable as it contributes to a false sense of security among users.
Don't all sites log IP addresses? No. All webservers are aware of the IP address of incoming connections, they could not work otherwise. However a webserver can be set up not to save this information to a file. All indymedia sites are meant to disable these logs and although the sysadmin (not site admin) could secretly switch this back on, that is not what this whole controversy is about. There would only be two or three sysadmins but there may be dozens of site admins and, in the case of the IMC UK website, those admins all had access to view IP addresses of people posting to the site. Indymedia UK repeatedly pointed out that their webserver did not log IP addresses but avoided revealing that any of its admins could peak at IP information whenever they wanted.
How does all this affect peoples security? Now this is almost properly out in the open there is hope that potential security will actually improve. Armed with knowledge of how disruptive indymedia posts are routinely being posted by malicious enemies within the state we are all better equipped to take everything from indymedia with a healthy pinch of salt. Likewise, any false sense of security should now have been shattered and users must now take full responsibility for their own security rather than relying on the indymedia collectives who have now all proved beyond doubt that they can not be trusted.
What about the future of indymedia? The forthcoming split hasn't been publicised much and perhaps that's because the details have not been sorted out. There is no guarantee that the group which wants to continue with the MIR based site, currently used for IMC UK, will actually be allowed to form as an official IMC collective in the UK. Even the date mentioned, May 1st, that may move forward or back. The new aggregation site, there appears to be no pilot site currently running so it's not clear whether it will be ready in time. Perhaps that's why only the Sheffield site has seen fit to tell its users about the big changes to come. The shake up may help resolve the impasse of distrust and hostility within the UK indymedia network itself but will probably do nothing to resolve the betrayal of trust the users are now aware of.
Chris
For fucks sake!
25.01.2011 13:01
NOT a police network
some of the GSi comments contained inside info only police would know...
25.01.2011 23:58
Can anyone who uses a library/council/jobcentre computer confirm it uses this gateway, by visiting a webpage that tells you your IP address, such as
anon
Some of the posts contained info only other activists would know
26.01.2011 13:45
The one that really stands out is the one from Denmark - apparently an activist got nicked over there and was shocked to find this fact published here before she got back - which is more likely, another activist posted the info or a danish cop took the trouble to tell a uk cop who then decided to publish the info?
Pay Attention
@Pay Attention
26.01.2011 16:19
Its clearly a rhetorical question supposed to suggest that it was an activist. Why that makes I have no idea.
Heres how FITWatch reported it:
" Similarly, a Fitwatch activist deported from Copenhagen after being caught up in the mass (unlawful) preventative arrests during the COP 15 protests, had the news – along with her name – posted on the then unmoderated site from the 303 gateway address"
The deportation was posted to Indymedia as well, again from the 303 gateway.
It seems entirely logical that the Danish police would contact the UK police before deporting an activist. And it isn't as if there would have been phones available to the activist during her detention. The number of activists who could have known about it is pretty limited.
Pay Attention gives us no real reason to think that this was the work of an activist.
At Ease!
I tend to agree with marker...
29.01.2011 17:55
Look, I think it is pretty much taken for granted that there is disinformation on the indymedia network. Just most of us are able to see through it TBH. Besides with undercover operatives operating within the activist community, I imagine most dis-information and agent provocateur activity will NOT be coming from an .gov gateway. If I were in charge of the security services my first target for an under-cover operative would be to place them within an indymedia collective, with instructions to get into an admin role, gain access to logs and the email networks that activists use. Just a thought.
jim
disinfo still
29.01.2011 18:41
Really, this stuff that libraries use it is bullshit - please justify that unsubstantiated crap,
unnecessary